Top Cybersecurity Threats and How to Protect Your Data in 2024

The digital landscape has been threatened massively by vicious malicious actors that hamper and malign the image of the targeted businesses. By keeping a watch on the latest infiltration in the industry, one can easily gauge the future trend and expedite moves appropriately. Global Cybersecurity scenes are grim as the cybercrime costs rates shall touch their all-time high at 9.5 trillion this year; which is only going to surge to USD 10.5 trillion by 2025 (Astrasecurity). With these rising trends in action, it is getting hard for businesses to guard their cyberspaces. It is essential to make way for the best-certified cybersecurity professionals who can leverage highly secured strategies for business growth. They can make available results with top cybersecurity certifications gracing their portfolio to allow an easy cyber guard plan. Let us take a dive in and enhance the sheer capabilities of countering these evolving cybersecurity threats.
What is a Cybersecurity Threat?
Cybersecurity threats are illegal acts performed by individuals with harmful intent, whose goal is to steal data, cause damage to, or disrupt computing systems or business infrastructure. Cybersecurity threats come in different sizes and impacts, including diversity in the form of malware, phishing, ransomware, supply chain attacks, and other malicious activity.
Why cybersecurity is important?
Cybersecurity is essential as it provides a guard against all sorts of data against data and information theft and loss. Sensitive data, protected health information, personally identifiable information, intellectual property, personal information, data, and government and business information systems are included. Improving organizational cybersecurity helps by:
- Protecting sensitive data
- Preventing financial losses
- Maintaining business continuity
- Building consumer trust
- Compliance with cybersecurity regulations
What to focus on cybersecurity in 2024?
McKinsey expects a 15% annual surge in cybersecurity costs. Business organizations are spending more on cybersecurity to manage the risks of an expanding attack surface; that is caused by the following factors:
- Increased teleworking
- Shift to the cloud
- Supply chain interactions
- Convergence of IT with OT and IoT
Latest Cybersecurity attacks news:
- 420 million cyberattacks were enumerated in the last year with 13 attacks per second being reported (Forescout Verdere Labs)
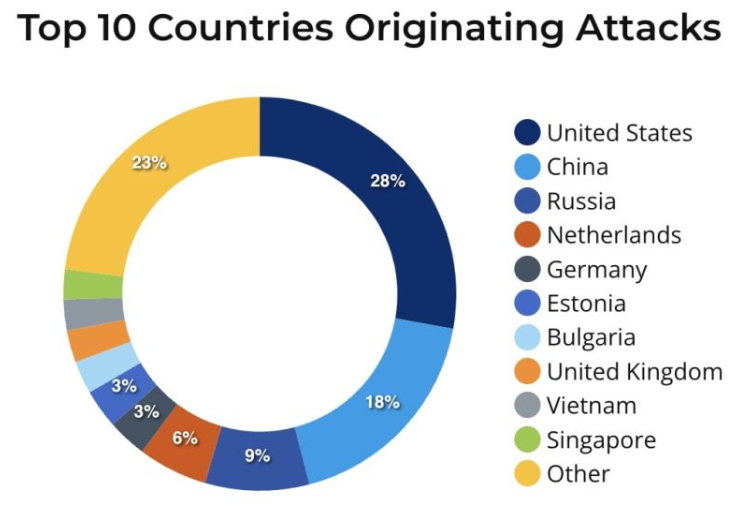
Source: Fore scout
- FBI states investment fraud tops the list of costliest cybercrimes
- Apple warns privacy danger lurking in push notifications
- A vending machine error revealed secret face recognition tech
- Apple blunts Zero-day attacks with iOS 17.4 update
- CISA outlines efforts to secure Open-Source Software
10 Current Cybersecurity Threats 2024 and Beyond:
- Diverse Cyberattacks
Malware, phishing, ransomware, web attacks, and other malicious software attacks are raging the cyberattack scenes. As per the Email Security Risk Report 2024, the top three phishing attack types are URLS, attacks sent from compromised trusted third-party accounts, and malware or ransomware. DMARC reveals the Netherlands to be the most targeted country with the highest volume of phishing attacks; followed by Russia, Moldova, the USA, and Thailand.
- Password attacks
Brute force attacks are among the most common and easiest methods for hackers to gain access to accounts. Password attacks account for 80% of the hacking breach.
- Insider threats
The Insider Threat Report 2023 by Cybersecurity Insiders states that 74% of organizations are at least moderately vulnerable to insider threats.
- Third-party cyber threats
ITGovernance.com research found 4645 publicly disclosed security incidents in January 2024 with 29530829012 data records known to have been breached.
- IoT Vulnerabilities
Viakoo.com predicts that 22% of organizations have had a serious or business-disrupting IoT security incident in the past year.
- Cloud-based Cyber-threats
Recent reports from expertinsights.com reveal the frequency of cloud attacks record showcases 45% of breaches being based on cloud.
- Geospatial threats
Cyberattacks for political purposes and cyberwarfare have become a major concern for global security. These attacks potentially cause significant damage to financial institutions, government agencies, and others.
- Deepfake technology
KPMG has brought forward a study that states that 95% of the 300 Canadian companies are currently experiencing fraud or have experienced severe deepfake fraudulent activities.
- Mobile security threats
The battle against mobile security theft is blazing beyond proportion with cybercriminals benefiting from the work-from-home world; that involves denial-of-service attacks and more.
- Intelligent Social Engineering
These include cybercriminals combining sophisticated social engineering with a variety of other types of attacks that make it impossible for employees to detect the infiltration in time.
12 Ways to Guard Businesses Against Cybersecurity Threats:
- Establishing a robust cybersecurity policy which starts with setting strong password policies and including multi-factor authentication
- Securing IoT connections with stringent security norms in place by enhancing the enterprise database security
- Deploying a people-centric security approach shall complement and work in tandem with a technology-centric approach; as 74% of the breaches involve a human element (Verizon).
- Controlled access to sensitive data offers growth opportunities for businesses as not all information or critical data is essential for employees to access.
- Managing passwords wisely involves using a different password for each account, having separate accounts for personal and business use, using mnemonics or lengthy passwords with special symbols, and more.
- Third-party users’ activity monitoring is deemed essential to safeguard organizational infrastructural
- Gartner suggests encrypting, masking, erasing, and resilience to enhance data protection and management
- Employing biometric security to ensure fast authentication, safe access, and precise employee identification
- Using multi-factor authentication assists in providing an extra layer of protection and security
- Conducting regular cybersecurity audits for timely detection of malicious activities
- Simplifying tech infrastructure by deploying all-in-one, lightweight, and easy-to-manage tools
- Supply chain risk management includes assessing risks, limiting access, collaboration, establishing a program and monitoring vendor’s activity
With these proactive stints, a cybersecurity expert with a cybersecurity certification and course can easily help build a sturdy guard against such malicious threat attacks. It is time to build security with such an explosive understanding of cyberattacks and the ways to counter them.